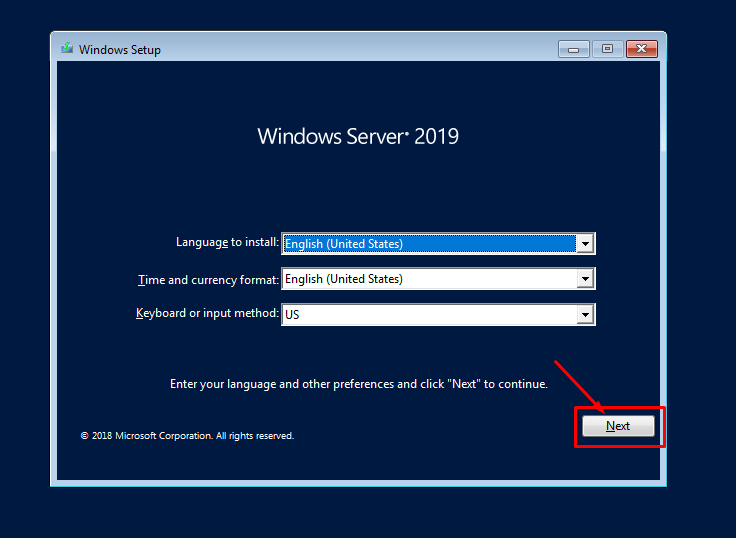
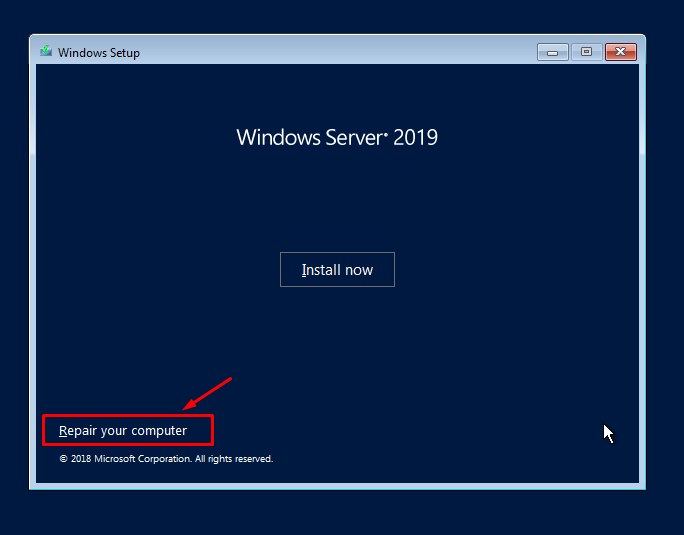
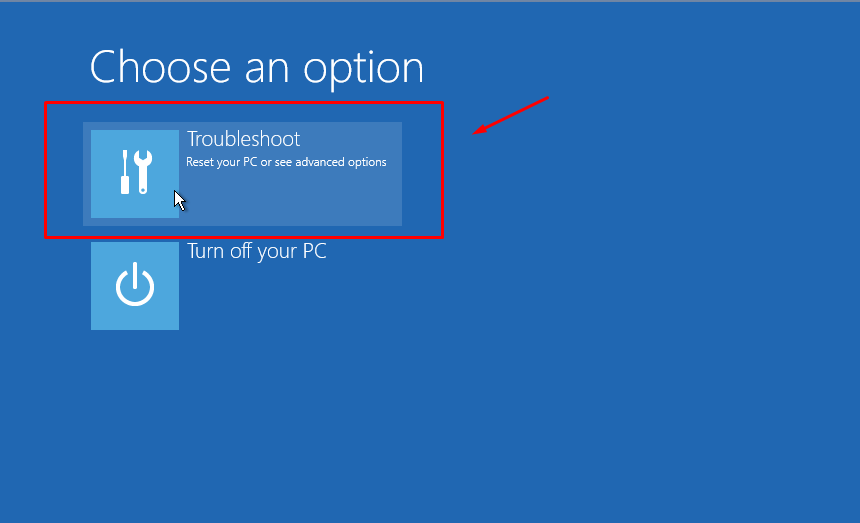
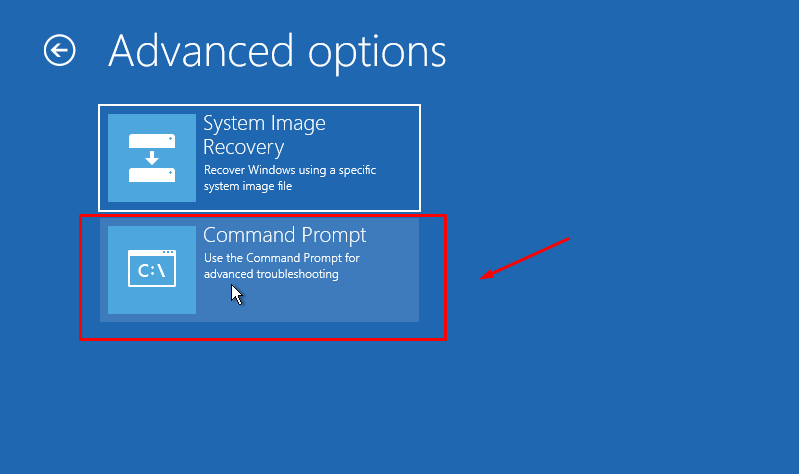
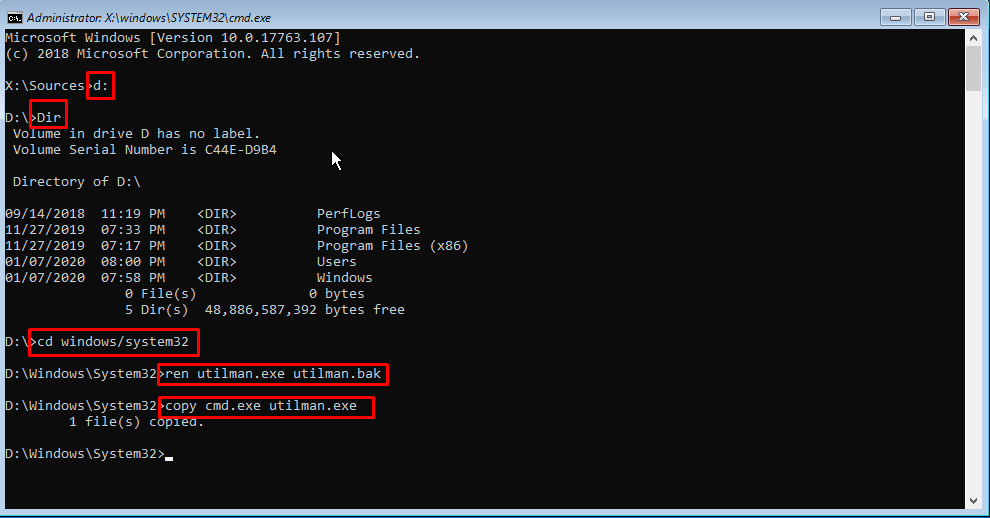
Back in December i replaced my Certificate on my VMWare Appliance with a our new Wildcard certificate.
But here in January, i got an alarm saying “Certificate Alarm” and it trigger it as an Alert.
Searching around for a solution, on what certificate that expire soon, i found this command:
for i in $(/usr/lib/vmware-vmafd/bin/vecs-cli store list); do echo STORE $i; /usr/lib/vmware-vmafd/bin/vecs-cli entry list --store $i --text | egrep "Alias|Not After"; done
It showing me that a backup mackine certificate is expiring
STORE MACHINE_SSL_CERT
Alias : __MACHINE_CERT
Not After : Jan 15 14:20:36 2022 GMT
STORE TRUSTED_ROOTS
Alias : b4a1550d09628bfe628d2685fe24f2b67afb9855
Not After : Jan 31 10:55:48 2025 GMT
Alias : 7a1f6edf1e16498c4eff9190fa5ef6742bbdde0e
Not After : Dec 4 14:03:36 2026 GMT
Alias : 909c4328a37dcff3d72de88c51df6f63600fc3f3
Not After : Dec 4 14:03:36 2026 GMT
Alias : 98c6a8dc887963ba3cf9c2731cbdd3f7de05ac2d
Not After : Nov 6 12:23:33 2027 GMT
Alias : 91c489ecb94b64e2eeffe438a0ad3fc1465959a2
Not After : Jan 15 14:20:36 2022 GMT
Alias : 4c27431717565a3a07f3e6d0032c4258949cf9ec
Not After : Feb 20 10:00:00 2024 GMT
Alias : b1bc968bd4f49d622aa89a81f2150152a41d829c
Not After : Jan 28 12:00:00 2028 GMT
STORE TRUSTED_ROOT_CRLS
Alias : bcd1699f713eabf1dbd8a21618ea6b0487adbdc8
STORE STS_INTERNAL_SSL_CERT
Alias : __MACHINE_CERT
Not After : Dec 4 14:03:36 2026 GMT
STORE machine
Alias : machine
Not After : Jan 31 10:55:48 2025 GMT
STORE vsphere-webclient
Alias : vsphere-webclient
Not After : Jan 31 10:55:48 2025 GMT
STORE vpxd
Alias : vpxd
Not After : Jan 31 10:55:48 2025 GMT
STORE vpxd-extension
Alias : vpxd-extension
Not After : Jan 31 10:55:48 2025 GMT
STORE SMS
Alias : sms_self_signed
Not After : Feb 3 11:51:48 2025 GMT
STORE BACKUP_STORE
Alias : bkp___MACHINE_CERT
Not After : Jan 20 12:00:00 2021 GMT
Alias : bkp_machine
Not After : Jan 31 10:55:48 2025 GMT
Alias : bkp_vsphere-webclient
Not After : Jan 31 10:55:48 2025 GMT
Alias : bkp_vpxd
Not After : Jan 31 10:55:48 2025 GMT
Alias : bkp_vpxd-extension
Not After : Jan 31 10:55:48 2025 GMT
So i exported this Machine certificate to a CRT file, and then deleted it with these commands
mkdir /certificates
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store BACKUP_STORE --alias bkp___MACHINE_CERT --output /certificates/old_machine.crt
/usr/lib/vmware-vmafd/bin/vecs-cli entry delete --store BACKUP_STORE --alias bkp___MACHINE_CERT -y
It then tell me that the certificate have been deleted
Deleted entry with alias [bkp___MACHINE_CERT] in store [BACKUP_STORE] successfully
Also running this command again
for i in $(/usr/lib/vmware-vmafd/bin/vecs-cli store list); do echo STORE $i; /usr/lib/vmware-vmafd/bin/vecs-cli entry list --store $i --text | egrep "Alias|Not After"; done
Show that the certificate have now gone.