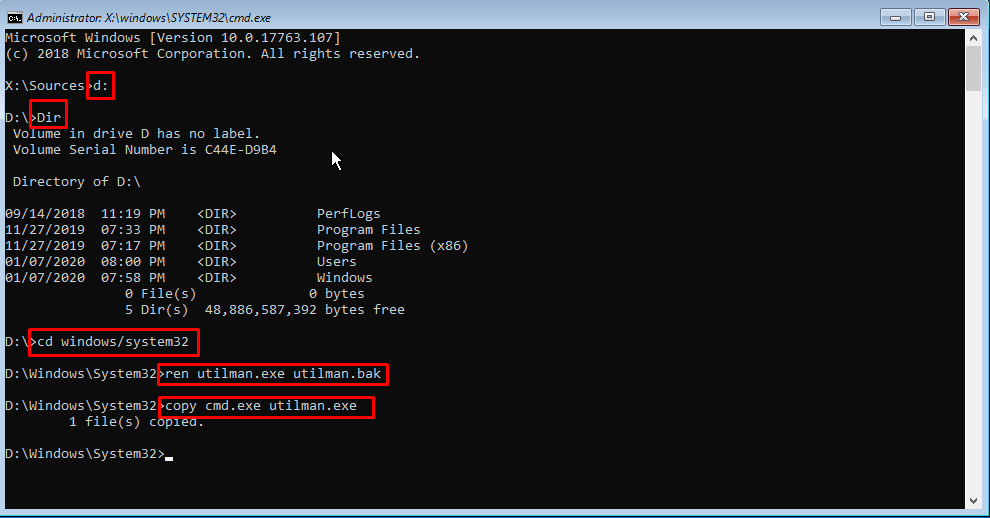
You can use this command to see the status of the Raid Controller and Raidset.
storcli /c0 showGenerating detailed summary of the adapter, it may take a while to complete. Controller = 0 Status = Success Description = None Product Name = Intel(R) RAID Controller RS3DC080 Serial Number = SK94678290 SAS Address = 500605b00f7ef7e0 PCI Address = 00:b5:00:00 System Time = 03/18/2022 15:44:57 Mfg. Date = 11/24/19 Controller Time = 03/18/2022 15:44:29 FW Package Build = 24.21.0-0126 BIOS Version = 6.36.00.3_4.19.08.00_0x06180203 FW Version = 4.680.00-8519 Driver Name = lsi-mr3 Driver Version = 7.702.13.00 Current Personality = RAID-Mode Vendor Id = 0x1000 Device Id = 0x5D SubVendor Id = 0x8086 SubDevice Id = 0x9360 Host Interface = PCI-E Device Interface = SATA-3G Bus Number = 181 Device Number = 0 Function Number = 0 Drive Groups = 1 TOPOLOGY : ======== ----------------------------------------------------------------------------- DG Arr Row EID:Slot DID Type State BT Size PDC PI SED DS3 FSpace TR ----------------------------------------------------------------------------- 0 - - - - RAID5 Optl N 5.451 TB dflt N N dflt N N 0 0 - - - RAID5 Optl N 5.451 TB dflt N N dflt N N 0 0 0 252:4 8 DRIVE Onln N 930.390 GB dflt N N dflt - N 0 0 1 252:5 9 DRIVE Onln N 930.390 GB dflt N N dflt - N 0 0 2 252:6 10 DRIVE Onln N 930.390 GB dflt N N dflt - N 0 0 3 252:7 11 DRIVE Onln N 930.390 GB dflt N N dflt - N 0 0 4 252:0 15 DRIVE Onln N 930.390 GB dflt N N dflt - N 0 0 5 252:1 12 DRIVE Onln N 930.390 GB dflt N N dflt - N 0 0 6 252:2 13 DRIVE Onln N 930.390 GB dflt N N dflt - N ----------------------------------------------------------------------------- DG=Disk Group Index|Arr=Array Index|Row=Row Index|EID=Enclosure Device ID DID=Device ID|Type=Drive Type|Onln=Online|Rbld=Rebuild|Dgrd=Degraded Pdgd=Partially degraded|Offln=Offline|BT=Background Task Active PDC=PD Cache|PI=Protection Info|SED=Self Encrypting Drive|Frgn=Foreign DS3=Dimmer Switch 3|dflt=Default|Msng=Missing|FSpace=Free Space Present TR=Transport Ready Virtual Drives = 1 VD LIST : ======= ------------------------------------------------------------- DG/VD TYPE State Access Consist Cache Cac sCC Size Name ------------------------------------------------------------- 0/0 RAID5 Optl RW Yes RWBD - ON 5.451 TB ------------------------------------------------------------- EID=Enclosure Device ID| VD=Virtual Drive| DG=Drive Group|Rec=Recovery Cac=CacheCade|OfLn=OffLine|Pdgd=Partially Degraded|Dgrd=Degraded Optl=Optimal|RO=Read Only|RW=Read Write|HD=Hidden|TRANS=TransportReady|B=Blocked| Consist=Consistent|R=Read Ahead Always|NR=No Read Ahead|WB=WriteBack| AWB=Always WriteBack|WT=WriteThrough|C=Cached IO|D=Direct IO|sCC=Scheduled Check Consistency Physical Drives = 8 PD LIST : ======= ------------------------------------------------------------------------------------- EID:Slt DID State DG Size Intf Med SED PI SeSz Model Sp Type ------------------------------------------------------------------------------------- 252:0 15 Onln 0 930.390 GB SATA SSD N N 512B Samsung SSD 870 QVO 1TB U - 252:1 12 Onln 0 930.390 GB SATA SSD N N 512B Samsung SSD 870 QVO 1TB U - 252:2 13 Onln 0 930.390 GB SATA SSD N N 512B Samsung SSD 870 QVO 1TB U - 252:3 14 UGood - 930.390 GB SATA SSD N N 512B Samsung SSD 870 QVO 1TB U - 252:4 8 Onln 0 930.390 GB SATA SSD N N 512B Samsung SSD 860 EVO 1TB U - 252:5 9 Onln 0 930.390 GB SATA SSD N N 512B Samsung SSD 860 EVO 1TB U - 252:6 10 Onln 0 930.390 GB SATA SSD N N 512B Samsung SSD 860 EVO 1TB U - 252:7 11 Onln 0 930.390 GB SATA SSD N N 512B Samsung SSD 860 EVO 1TB U - ------------------------------------------------------------------------------------- EID=Enclosure Device ID|Slt=Slot No.|DID=Device ID|DG=DriveGroup DHS=Dedicated Hot Spare|UGood=Unconfigured Good|GHS=Global Hotspare UBad=Unconfigured Bad|Onln=Online|Offln=Offline|Intf=Interface Med=Media Type|SED=Self Encryptive Drive|PI=Protection Info SeSz=Sector Size|Sp=Spun|U=Up|D=Down|T=Transition|F=Foreign UGUnsp=Unsupported|UGShld=UnConfigured shielded|HSPShld=Hotspare shielded CFShld=Configured shielded|Cpybck=CopyBack|CBShld=Copyback Shielded Cachevault_Info : =============== --------------------------------------------------------- Model State Temp Mode MfgDate Next Learn --------------------------------------------------------- CVPM02 Optimal 23C - 2020/04/09 2022/03/31 00:41:59 ---------------------------------------------------------
Here you can see under PD List, that drive 252:3 14 stand as UGood. Thats the new disk i have put into the server, and have been detected by the raidset.
To include this disk into the array that you see under VD List, you need to do this
storcli /c0/v0 start migrate type=raid5 option=add drives=252:3This will add the disk to the raidset. This can takes hours and even days, if you have a big raidset.
You can check the status with this command:
storcli /c0/v0 show migrateController = 0 Status = Success Description = None VD Operation Status : =================== ------------------------------------------------------------ VD Operation Progress% Status Estimated Time Left ------------------------------------------------------------ 0 Reconstruction 2 In progress 9 Hours 52 Minutes ------------------------------------------------------------ DG=Arrays | Slot=Drive Bay No|VD=Virtual Drive/Logical Drive|EID=Enclosure Device ID
Here you can see that it will take 9 hours and 52 minutes to complete the Reconstruction
When it done with the reconstuction, the command from before will output this:
VD Operation Status : =================== ----------------------------------------------------------- VD Operation Progress% Status Estimated Time Left ----------------------------------------------------------- 0 Migrate - Not in progress - -----------------------------------------------------------
And then you can check the array with the command from the top of this guide
storcli /c0 showAfter this you need to change the partition table, and then expand the volume.